Mobile App Threats Are Playing Hide and Steal

Image Source: Kaspersky
In May 2019, a famous graphic design tool Canva suffered an attack that exposed 137 million user accounts including usernames, cities, email addresses, and salted and hashed with bcrypt passwords.
Canva said that hackers managed to view, but not steal user data.
This was the attack on a popular graphic design tool Canva that shocked its users who were using its mobile app and website.
As the demand for mobile apps is growing in every industry vertical, mobile app security concern is taking higher priority. Cyber or malware attack is the greatest security breach that no company or businesses want to put their app security at risk.
Your app’s success is green until it encounters security threats. Therefore, it becomes highly essential to secure your mobile app that is fully protected against any possible threats or malware attacks.
In this blog, we will tell you great tips on how to ensure your mobile app security and how developers should manage security issues from the initial stage of app development.
If you are:
- Using multiple apps in your smartphone
- Mobile app development company want to build apps with strong data protection features
- Business owner willing to enhance business growth with a mobile app without compromising data security
This blog is for you.
So, let’s begin.
Table of Contents
ToggleWhat is Mobile App Security?
Mobile app security is a method to protect applications from unauthorized access or external threats such as malware and other digital frauds that risk sensitive user’s information.
Why You Should Take Mobile App Security More Seriously?
Think the number of apps on Google Play Store. There are 2.87 million apps on Google Play Store that are competing with each other in different scales to market their brand.
If you are a mobile app development company or a professional app developer, you want to make sure the app that you are creating for your client or customer doesn’t comprise any security issues.
Otherwise, it will hamper the entire app development project and may lead to losing the client and company’s reliability forever. Thus, app developers should take app security on the top priority.
Here are some data that reveals the increment of malware attacks in mobile apps for the past few years.
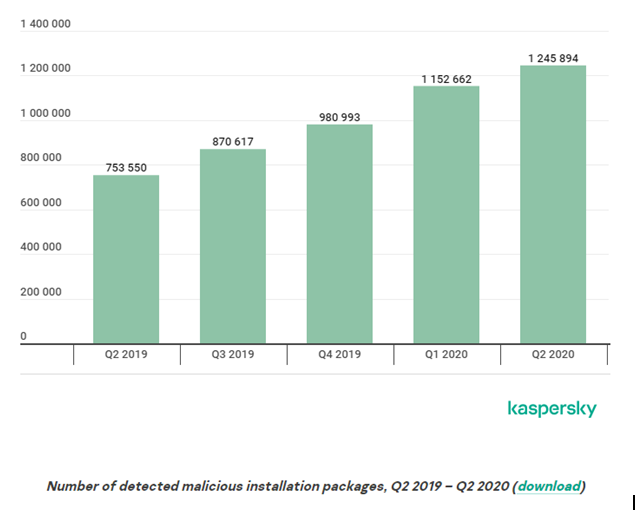
Data Source: Kaspersky
In 2020, Kaspersky detected 1,245,894 malicious installers on mobile devices, which is an increase of 93,232 over the previous quarter.
When you build a social media app, mobile payment app, or business app, your app ask user for their personal information. This makes both mobile app and user’s privacy vulnerable. Today hackers are very skilled to decode encryption.
Threats may not always stealing username and password or sending phishing emails. It may be monitoring private chats or listening to conversations as well.
Therefore, staying one step ahead is not the choice but a necessity for proving the best security features to your mobile app.
Common Mobile App Security Risk
- Improper Platform Usage
- Insecure Data Storage
- Insecure Authentication
- Insecure Communication
- Insufficient Cryptography
- Insecure Authorization
- Poor Code Quality
- Code Tampering
- Reverse Engineering
- Extraneous Functionality
Android App Security Risk
- Reverse Engineering
- Insecure Platform Usage
- Ignoring Updates
- Rooted Devices
iOS App Security Risk
- Jailbreak
- User Authentication
- Insecure Data Storage
What Are The Mobile App Security Risks That Developer Watch Closely?
Reverse Engineering
Most Android apps are created in Java with an Integrated Development Environment (IDE) like Eclipse. There are various tools available on the Internet that can reverse Java apps.
Reversing Android apps can easily disclose test login credentials, insights into bad design, details about the type of encryption used in the app, and about the libraries.
This technique helps attackers to hack not only one device but also multiple devices using the same decryption method. So, your own code can be utilized against you and weaken the door for hackers.
Insecure Platform Usage
Android OS and apps get vulnerable when app developers ignore the best coding practices suggested by Google to communicate with its mobile OS, especially through unsecure Android intents and platform permissions.
For example, when developer does not protect exported services or issues a wrong flag to an API call, their apps remain exposed to external threats. It makes easier for hackers to snoop on Android devices to receive Broadcast Receiver instances that are meant for legitimate apps.
App developers sometimes ignore the use of Local Broadcast Manager to communicate to legitimate apps, hence creating a security risk.
Insecure Data
Majority of apps store data in SQL databases, binary data stores, cookies, and common text. These storage locations can be accessed by external attempts when the operating system, compiler, or framework is not strong.
Reports have found that insecure data storage is one of the most common issues in iOS devices that allow external sources to steal critical information of app and users.
Lack of Encryption
Encryption is a technique of transporting data in ciphered code that cannot be viewed without matching with a secret key.
As per the data by Symantec, around 10.5% of enterprise devices and 13.4% of consumer devices do not have encryption enabled, that causes exposing sensitive data as plain text.
Malicious Code Injection
User forms are easily utilized to inject malicious code and access the server data. For an instance, some apps do not restrict the characters that a user can input in a field.
Eventually, it allows hackers to inject a line of JavaScript into the login form and get access to confidential information.
Binary Planting
This is a common term where hacker puts a binary file including malicious code on a local file system in the mobile device and then uses it to access the control over the device.
It can be done with a malicious SMS or forcing the user to click on external links. So in this way, mobile app security gets compromised.
Mobile Botnets
Mobile botnets aim to get complete control over the device and used to send text messages, email, make calls, and access user data like photos and contact lists. This is a kind of bots which run on IRC networks developed with the help of Trojans. When an infected app connects to the Internet, it starts to work as a client and sends information to a server.
Mobile App Security Best Practices for Developers
- Allow Minimum App Permissions
- Secure Sensitive Information
- Add Certificate Pinning
- Apply Signature-Based Permissions
- Not Saving Passwords
- Implement Session Logout
- Enable Multi-Factor Authentication
- Use Penetration Testing
- Use Third-Party Libraries with Precaution
- Session Handling
- Manage Keys Safely
- Use HTTPS over HTTP
- Encrypt Cache
- Apply RASP Security
- Use Code Obfuscation
Best mobile app security practices help to ensure the app is totally risk-free and does not let the user data be accessed by external source. Therefore it is important to ensure all security checks are performed well before the app is launched on the app store for public use.
Here are useful tips for developers to make sure that their app does not comprise any security issue.
A good programmer is someone who always looks both ways before crossing a one-way street. – Doug Linder
1. Allow Minimum App Permissions
Permissions allow app to operate more effectively. But, at the same time, they put apps at risk of external attacks. No app should ask permission request beyond its functional or required limit. Developers can recycle their existing libraries but create new ones that specifically ask permission.
2. Secure Sensitive Information
Set a proper mechanism in the app to secure the critical data that are prone to attacks. Hackers can extract sensitive information by reverse-engineering codes. Developers should cut down the data stored as max as possible to minimize the risk.
3. Add Certificate Pinning
Certificate pinning is an operating method that enables apps to defend against man-in-the-middle threats when device is connected to unsecured networks. However, this technique has some limitations. In few cases, it may not help network detection and response tools as traffic inspection gets a tougher task.
There are certain browsers that do not aid certificate pinning, making life harder for hybrid apps to work.
4. Apply Signature-Based Permissions
When you share data between two apps that you own or control, apply signature-based permission to this process. Signature-based permissions don’t need user confirmation and instead allow the app to access the data when it is signed using the same signing key.
It makes data protection strong. Hence, these permissions give a streamlined and safe user experience.

5. Not Saving Passwords
Various apps ask users to save passwords to prevent them from repeatedly inserting the login details. In case of mobile theft, these passwords can be used to access personal data. In the same way, if the password is saved in an encrypted format, the security risk gets higher. Therefore, developers try to avoid saving passwords on mobile devices.
Instead of this, they can store the password on the app server. This allows affected users to change the passwords by logging on to the server, even if the mobile device is stolen.
6. Implement Session Logout
Users are generally found forgetting to log out of the website or app they are using. Therefore, mobile payment apps should enable the automated session logout function to end the session of a user after a certain time of inactivity.
Developers must implement session logout on all m-commerce apps, mobile banking apps, and e-commerce app that are dedicated to payment process.
7. Enable Multi-Factor Authentication
Multi-factor Authentication creates an extra layer of security whenever a user logs into app. This method also covers weak passwords that can be easily guessed.
Multi-factor Authentication gives a secret code that must be entered along with the password to log into the app. This code can be sent through SMS, email, biometric methods, or Google Authenticator.
8. Use Penetration Testing
Penetration testing is a useful technique to figure out vulnerabilities in an app. It focuses to find potential security risks that an attacker or malware might use. It includes checking unencrypted data, third-party permissions, weak password policy, no password expiry protocol, etc.
Many experienced app developers perform penetration testing frequently to keep the app security fully ensured.
9. Use Third-Party Libraries with Precaution
Many developers use third-party libraries to reduce the amount of coding and ease app development process. But, this may be a risky step.
For example, the GNU C library had a security flaw which allowed buffer overflow, this created security risk as any attacker could remotely execute a malicious code and access the vital data.
Hence, developers should wisely use or limit the use of third-party libraries and develop a policy for managing libraries to prevent apps from external threats.
10. Session Handling
Sessions on mobile devices last longer than desktops and as a result, it increases the server load. Using tokens in the place of device identifiers to make a session could a better option.
Token is easier to revoke whenever requires and even highly secure in case of stolen device. Developers can also consider session expiration as an alternative. Making remotely wiping of data for the lost or stolen device is better option to keep this feature in the app.
11. Manage Keys Safely
Key management is a critical aspect of encryption. Hard coding keys are not good to the app’s security and developers should avoid this. If someone steals the key, anyone can get control of the device.
Thus developers should try to store the keys in a safe container, not on the users device. There are some popular cryptographic protocols for this goal such as MD5 hash and SHA1. Developers should use the modern encryption standards and APIS, like 256-bit encryption with SHA-256 hashing.
12. Use HTTPS over HTTP
HTTPS is Hypertext Transfer Protocol Secure which is contrasted with HTTP communication. HTTPS provides the security of data when it is transmitted over the Internet or any network. This communication protocol is encrypted by Transport Layer Security (TLS).
TLS and Secure Socket Layer (SSL) are cryptographic protocols that secure data privacy over several communication channels. TLS uses X.509 certificates, an exchanged symmetric key, public or private key encryption that allows to:
- Validate the authenticity of communication
- Verify a server’s identity
- Encrypt the communication
- Secure the messages from external monitoring
On the other side, HTTP data is unencrypted, unverifiable, and invalidated which allows hackers to snoop on user account. Developers here must ensure a valid SSL certificate on the server to which the app is connected and exchange data between the server and the app only using HTTPS protocol.
13. Encrypt Cache
Cache is a software component that secures the data temporarily on the device. It is used to prevent the delay of data retrieval. Developers should encrypt cache otherwise if the app does not erase its data after the session ends, and cache not expired, malware, or an unknown attack can manipulate it to access user data or the server.
14. Apply RASP Security
RASP stands for Runtime Application Self-Protection, which protects an app from runtime attacks. RASP is security software that combines with app or its runtime environment and consistently intercepts calls done to the app from possible threats.
It automatically analyzes the incoming traffic and stops fraudulent calls from working inside the app. Every incoming request goes through the RASP layer implemented between the app and the server.
15. Use Code Obfuscation
Code Obfuscation is considered among the best way to protect an app from hackers. This is a technique of creating a code that is complex for hackers to understand.
Code Obfuscation has become famous in recent times and now widely used to conceal code from external view. Obfuscators automatically convert programming code into a format that humans find very difficult to read. Code Obfuscation contains:
- Encrypting some part or the complete code
- Erasing metadata that may expose information about the libraries or APIs used in the app
- Renaming variables and classes in meaningless labels so they are impossible to be guessed
By obfuscating code, it prevents app data and property from hackers who might reverse-engineer code using different software programs.
In iOS, this method is not much popular as its libraries are not opened. On the other side, Android has open-source libraries. Therefore, it is critical for Android app developers to obfuscate the app code.
Conclusion
Businesses should comprehend that the effect of mobile app security goes beyond user security and impacts the reputation of your company overall.
As the number of hacking attempts and data breaches is increasing, users are now much aware of mobile app security issues and choose apps which are safe over those that can secure their information. After all, security is more important than anything.
Thus, mobile app developer endeavors to develop apps that satisfy the user requirements and aim to the various app security aspects.
Having said that, it’s time to hand over the mike to you.
Are you aware of how much your app is secure? Or
If you are a developer, what challenges you face while strengthening app security?
Share your views here in the comment box if you find useful for our audience.
Or we can also help you in building advanced mobile apps using modern technologies which are fully secured against any attacks and malware.